In today’s hyperconnected world, securing your digital identity is more critical than ever. Cyberattacks, data breaches, and phishing scams are constantly evolving, putting your online accounts at risk. Even strong passwords aren’t enough on their own anymore. That’s where two-factor authentication (2FA) comes in a powerful and increasingly essential layer of protection.
In this guide, we’ll explain how to create strong two-factor authentication, the different types available, and how to set it up across your most important accounts. Whether you’re a beginner or someone looking to improve your online security, this two-factor authentication guide will walk you through everything you need to know.
What Is Two-Factor Authentication?
Two-factor authentication is a security process that requires users to verify their identity using two separate methods before gaining access to an account. Typically, it combines:
-
Something you know (like a password)
-
Something you have (like a smartphone or hardware token)
or -
Something you are (like a fingerprint or facial recognition)
The main benefit of 2FA is that even if your password is compromised, a hacker still can’t access your account without the second factor. This makes it far more secure than relying on passwords alone.
Why Is Two-Factor Authentication Important?
Using strong two-factor authentication significantly reduces the risk of unauthorized access. Hackers often rely on stolen passwords, phishing, or credential stuffing. But with 2FA in place, those credentials are useless without the second verification step.
Key benefits of 2FA include:
-
Increased account security
-
Protection against phishing and keylogging attacks
-
Added safety for sensitive data (banking, email, cloud storage)
As cybercrime becomes more sophisticated, 2FA is one of the simplest and most effective tools for protecting your digital life.
Types of Two-Factor Authentication
Before you set up 2FA, it’s important to understand the different options available. Not all two-factor authentication methods offer the same level of security.
1. SMS-Based 2FA
With SMS 2FA, a code is sent to your mobile phone via text message when you try to log in. You enter the code after your password to verify your identity.
Pros:
-
Easy to set up
-
Doesn’t require additional apps
Cons:
-
Vulnerable to SIM swapping and interception
-
Less secure than other 2FA methods
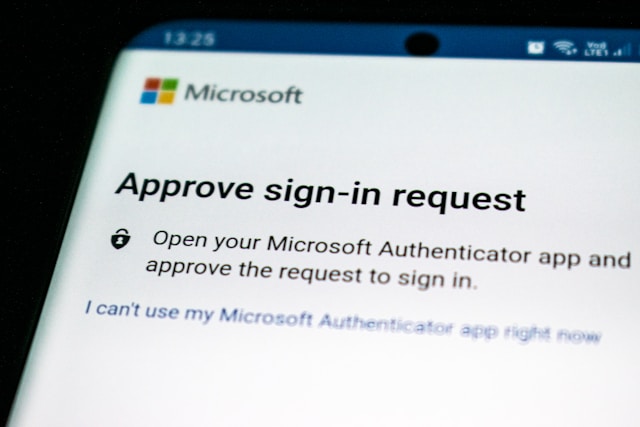
2. App-Based Authentication
Authenticator apps like Google Authenticator, Authy, or Microsoft Authenticator generate time-based one-time passwords (TOTP) that expire after a short time.
Pros:
-
More secure than SMS
-
Works even without mobile signal
Cons:
-
Requires installation of an app
-
If you lose your phone, you need backup codes
3. Hardware Security Keys
Devices like YubiKey or Google Titan Security Key are physical devices you plug into your computer or tap on your phone to verify your identity.
Pros:
-
Extremely secure
-
Resistant to phishing and remote attacks
Cons:
-
Not free
-
You need to carry the key with you
4. Biometric Authentication
Some systems use fingerprints, facial recognition, or retinal scans as a second factor. This is often combined with mobile devices or apps.
Pros:
-
Convenient and fast
-
Unique to the user
Cons:
-
May not be supported on all devices
-
Can be spoofed with advanced tech
How to Create Strong Two-Factor Authentication
Setting up secure 2FA methods is simple, but you need to do it right. Here’s how to set up 2FA on your accounts with maximum protection:
Step 1: Use a Strong Password First
Before enabling 2FA, make sure your password is strong. Use a combination of:
-
Upper and lowercase letters
-
Numbers
-
Special characters
-
A password manager to generate and store passwords
Never reuse passwords across sites.
Step 2: Choose the Most Secure 2FA Option
Avoid SMS-based 2FA when possible. Instead, opt for:
-
App-based authentication (e.g., Google Authenticator)
-
A hardware security key if available
-
Biometrics (if supported and trusted)
Step 3: Set Up the Authenticator App or Device
Follow the instructions for your chosen platform:
-
Go to the security settings of your account (Google, Facebook, Amazon, etc.)
-
Select two-factor authentication
-
Choose your method (app, key, or SMS)
-
Scan the QR code or link the device
Step 4: Store Backup Codes or Recovery Options
Many services offer one-time-use backup codes. Save these in a safe place. Without them, you might get locked out if you lose your 2FA device.
Step 5: Test the Setup
Before logging out, test your new 2FA setup to make sure everything works as expected.
Best Practices for Using 2FA
Once you’ve set up strong two-factor authentication, follow these best practices to stay safe:
-
Enable 2FA on all sensitive accounts (email, cloud storage, financial platforms, etc.)
-
Avoid using SMS if better options are available
-
Keep backup codes secure and private
-
Don’t approve unknown login attempts
-
Be cautious of phishing emails mimicking 2FA prompts
-
Regularly update your authenticator apps and devices
2FA for Businesses and Teams
For organizations, using two-factor authentication is a critical part of a strong cybersecurity strategy. Here’s why:
-
Protects company data from breaches
-
Secures employee accounts and email systems
-
Reduces risk from weak or shared passwords
Companies can use centralized 2FA management tools, like Duo or Okta, for scalable deployment. Educate employees on how to use 2FA and train them to spot suspicious login prompts or scams.
Common Mistakes to Avoid
Even with 2FA, there are some common pitfalls to avoid:
-
Using the same password across accounts
-
Failing to store backup codes
-
Relying only on SMS 2FA
-
Not updating or rotating 2FA keys or apps
-
Clicking fake verification links
By avoiding these, you’ll make your account security even stronger.
Conclusion
Knowing how to create strong two-factor authentication is one of the most effective steps you can take to protect your digital identity. Whether you’re using a free authenticator app or investing in a hardware key, taking that extra verification step can stop hackers in their tracks.